
TELEPORT ACCESS PLATFORM
Teleport Access
On-demand, least privileged access on a foundation of cryptographic identity and zero trust

Trusted by Market Leaders


















The Growing Infrastructure Problem
Distributed infrastructure, cloud computing, and DevOps have changed how we build and deploy applications. Access to infrastructure hasn't kept up. Engineers and security teams struggle with the complexity and attack surface of access silos, shared credentials, long-standing privileges, and insecure protocols.

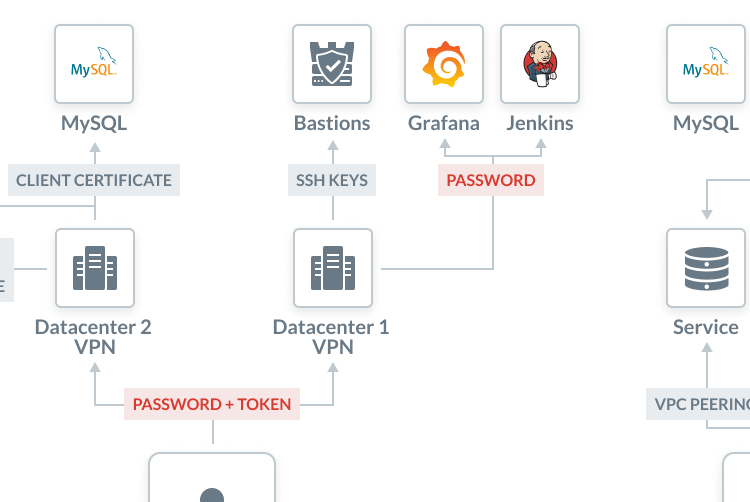
Streamline complexity and protect your infrastructure with Teleport Access
Phishing-Resistant Identity
Lock down attack surfaces at every level of your infrastructure with cryptographic identities assigned to users, machines, and workloads. Teleport eliminates credentials, the #1 source of data breach.
User Identity
Authenticate users without passwords leveraging Touch ID, YubiKey Bio and other biometric devices. Add Teleport as a security layer on top of your identity provider or use Teleport's SSO.
Machine Identity
Issue and govern identities for your CI/CD automation systems, service accounts and microservices leveraging HSM and KMS. Machine ID can be hardened by HSM or virtual HSM.
Resource Identity
Assign a cryptographic identity to every application, server, and database to gain visibility and control of all your infrastructure.
Device identity
Assign identities to enrolled TPM-equipped client devices (laptops, workstations, YubiKeys, and more)
Unified Access
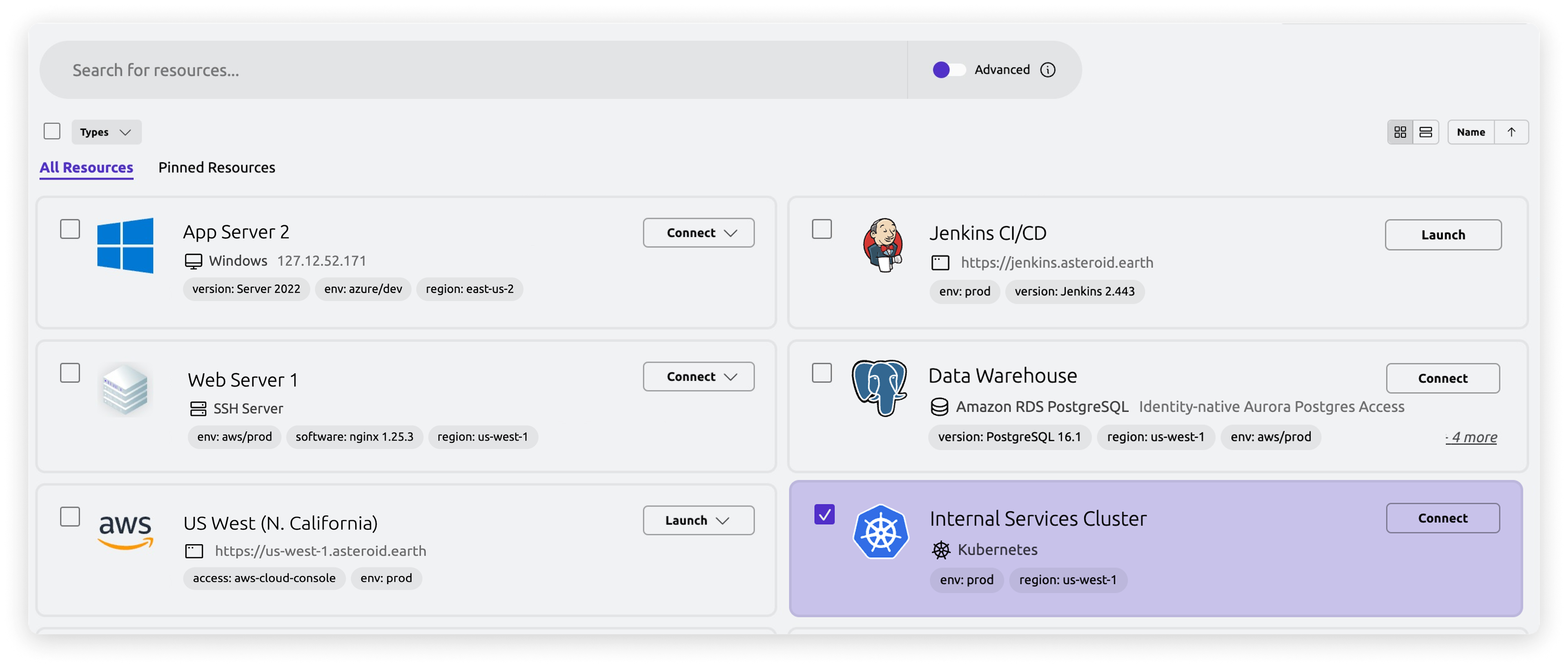
Break access silos with a unified inventory of all infrastructure resources in your organization. Eliminate the need for different access paths, passwords, shared secrets, vaults, and VPNs.
Trusted Infrastructure
Self-updating inventory of trusted computing resources (servers, clouds, databases, Kubernetes clusters, Web apps) and enrolled TPM-equipped client devices (laptops, workstations, YubiKeys, and more)
Secure Remote Access
Zero-trust access to applications and workloads from anywhere, with auditable access across clouds, on-premises environments and IoT fleets, without VPNs, bastion hosts or vaults with shared secrets.
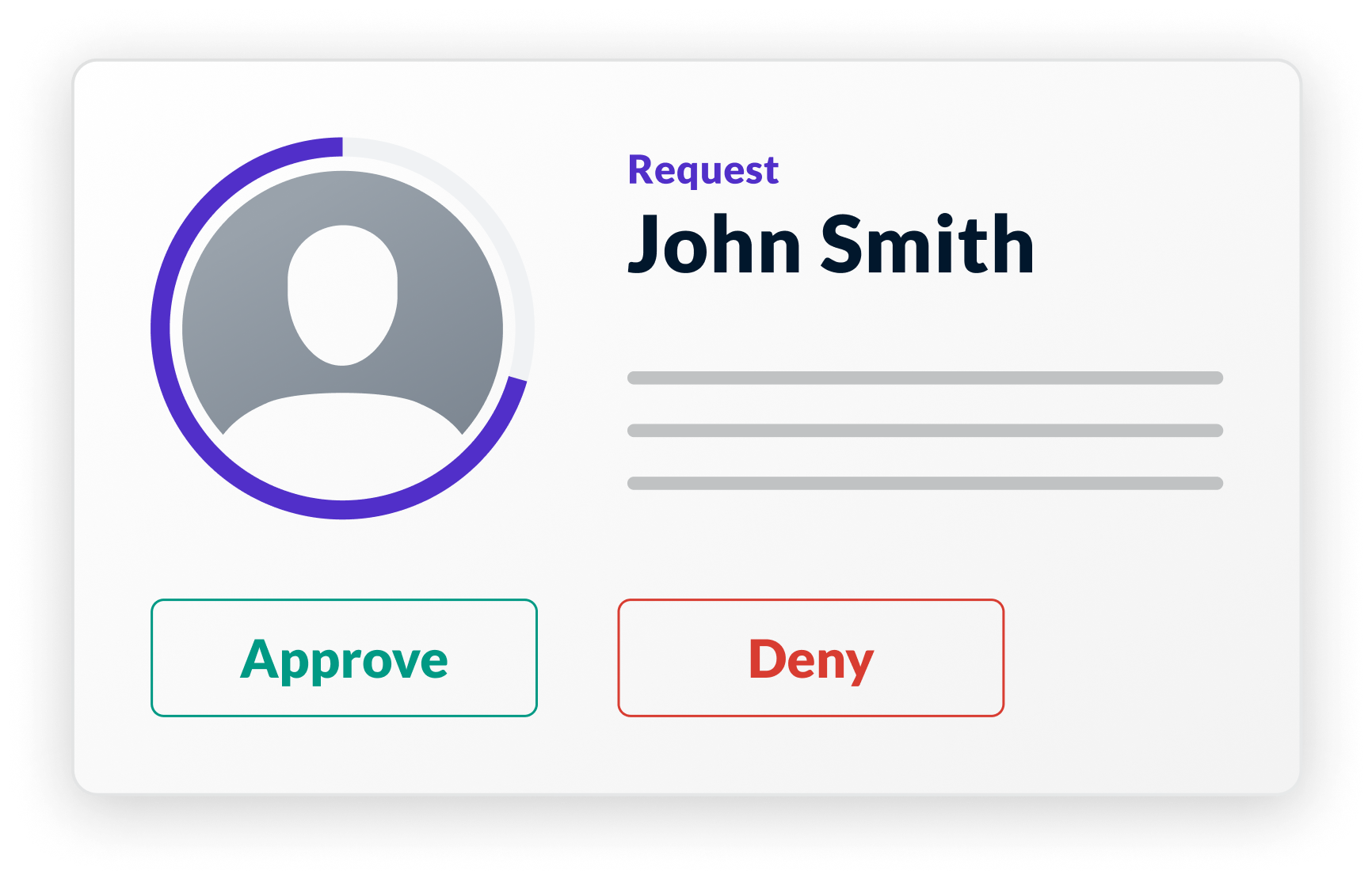
Ephemeral Privileges
Enforce the practice of least privileged access and lower the operational overhead of managing privileges or enforcing policy.
Short-lived Privileges
Temporary access is granted through short-lived certificates bound to biometric devices and secure-enclaves, via Teleport’s built-in certificate authority for X.509 and SSH certificates for all resources, including legacy systems.
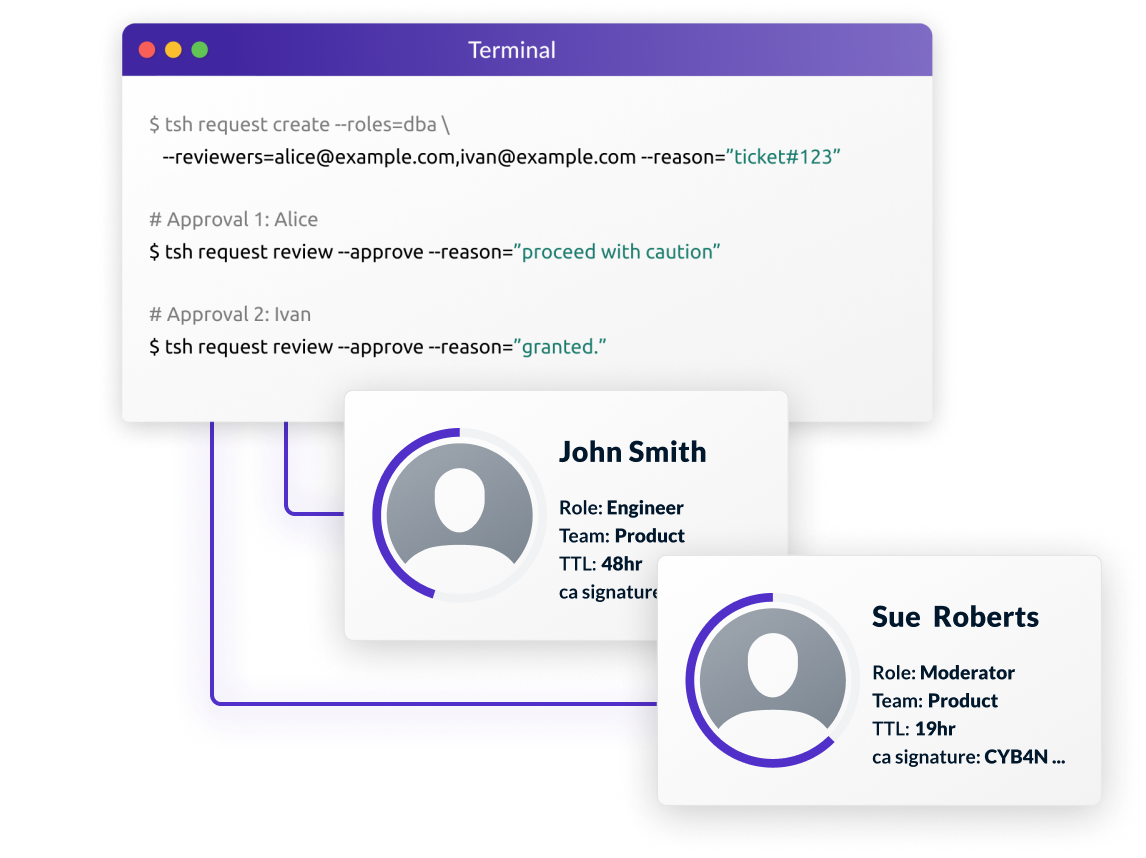
Access Requests
Temporarily provision minimal privileges to complete a task, through manual review or predefined workflows. (available in Teleport Identity).

Consolidated Visibility & Audit
Collect all events generated by humans and machines across your entire infrastructure in one place and export to any SIEM or threat detection platforms for further analysis.
Identity-Based Audit Events
Collect structured, detailed audit events for each session with identity, application and protocol data.
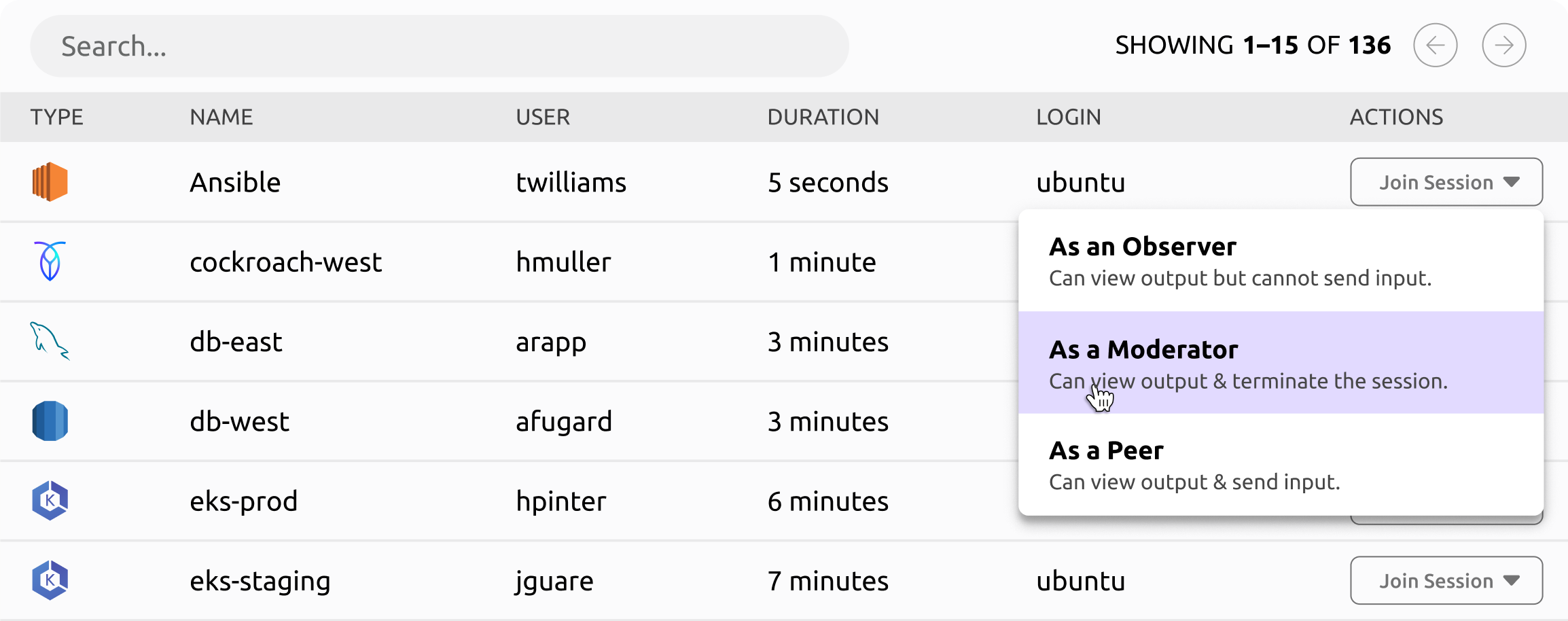
Interactive Session Controls
Record, replay, join, and moderate interactive sessions for SSH and Kubernetes.
Live Sessions View
View every active authenticated connection across your entire infrastructure. Interfere if needed.
Compliance & Policy
Enforce access policy and workflows to comply with regulatory or corporate policy frameworks.
Dual Authorization
Require approval by multiple authorized team members for highly privileged actions (as required by FedRAMP AC-3 and SOC 2).
Session Sharing and Moderation
Require your highly privileged sessions to always include a moderator to prevent production and security incidents.
Supports Regulatory Standards
FedRAMP, SOC 2, HIPAA, PCI, ISO 27001
AI Assist
Chat with your infrastructure fleets, when natural language is better than SSH or bash. (Note: Experimenal. Use caution and validate all outputs.)
 Troubleshoot Common Issues
Troubleshoot Common IssuesDebug issues with suggested generated commands and scripts based on your infrastructure.
 Optimize Infrastructure
Optimize InfrastructureAnalyze performance data, usage patterns, resource allocations, and system loads.
 Collect Infrastructure Details
Collect Infrastructure DetailsGenerate commands to help you answer common questions about your infrastructure.
 Run Generated Commands
Run Generated CommandsReview, verify, and then execute generated commands on target infrastructure.
Problems Customers Solve with Teleport

Improve Engineer & Workforce Productivity
- Improve on-boarding and offboarding
- Eliminate access silos
- Adopt on-demand and just-in-time access
- Eliminate VPNs and bastion hosts
- Unify user and machine access

Protect Infrastructure from Identity Attacks
- Eliminate credentials & standing privileges
- Eliminate backdoor access paths
- Monitor access patterns and respond
- Apply policy/remediate instantly across all infrastructure

Meet Compliance Requirements
- FedRAMP
- SOC 2
- HIPAA
- PCI
- ISO 27001
What Our Customers Say
Learn More
TELEPORT ACCESS PLATFORM
Teleport Access
On-demand, least privileged access, with identity security and zero trust
Teleport Identity
Harden your infrastructure with identity governance and security
Teleport Policy
Unify and control access policies across all of your infrastructure